Hackers Are Hijacking NGINX Servers Without Installing Malware
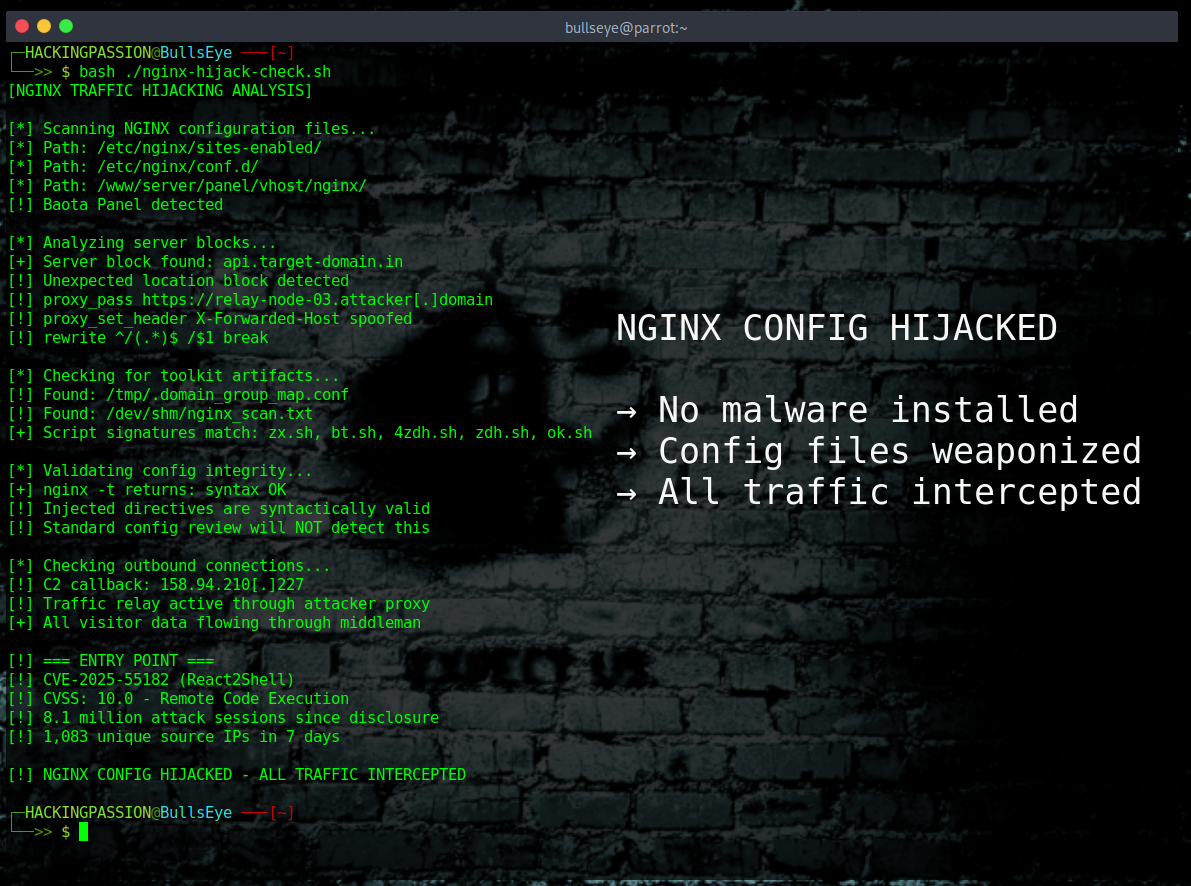
Hackers are hijacking NGINX web servers and rerouting live traffic through their own infrastructure. No malware installed, no vulnerability exploited. Just a few lines changed in a configuration file, and every visitor’s data flows through attacker-controlled servers without anyone noticing. 🧐
NGINX is the most popular web server on the planet. It powers over 5 million websites and handles roughly one in three web connections worldwide. Banks, governments, and universities all depend on it. And right now, a campaign is silently turning these servers into traffic relays.