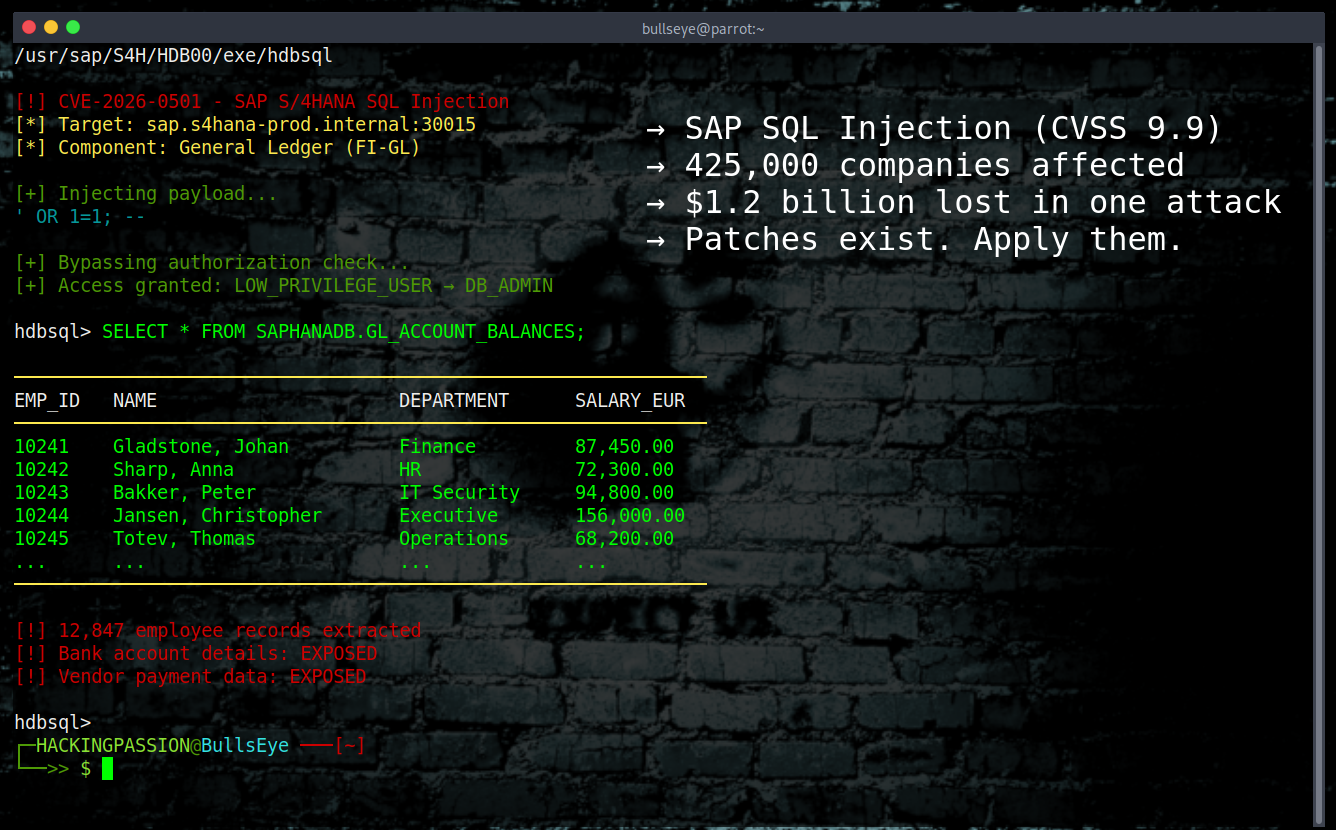
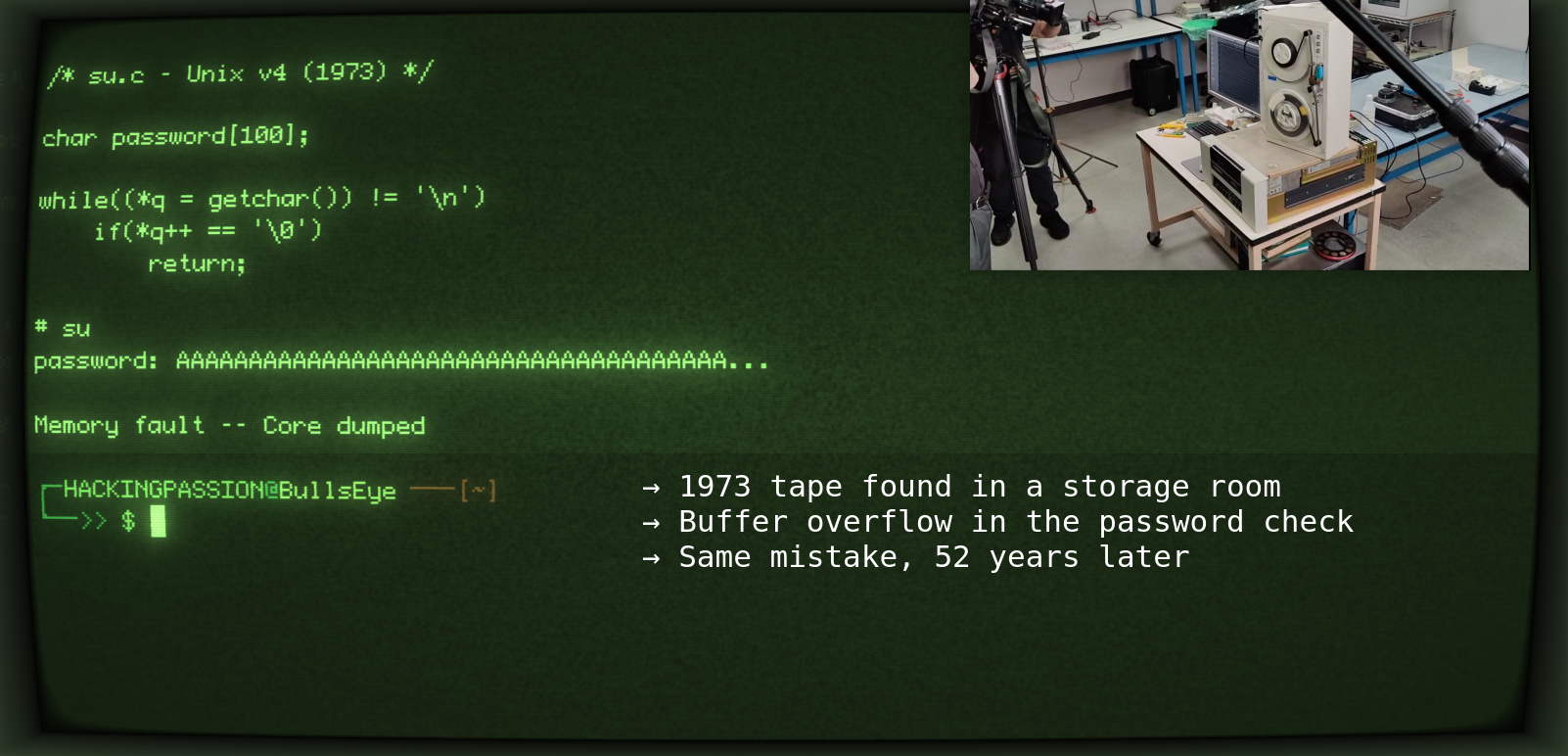
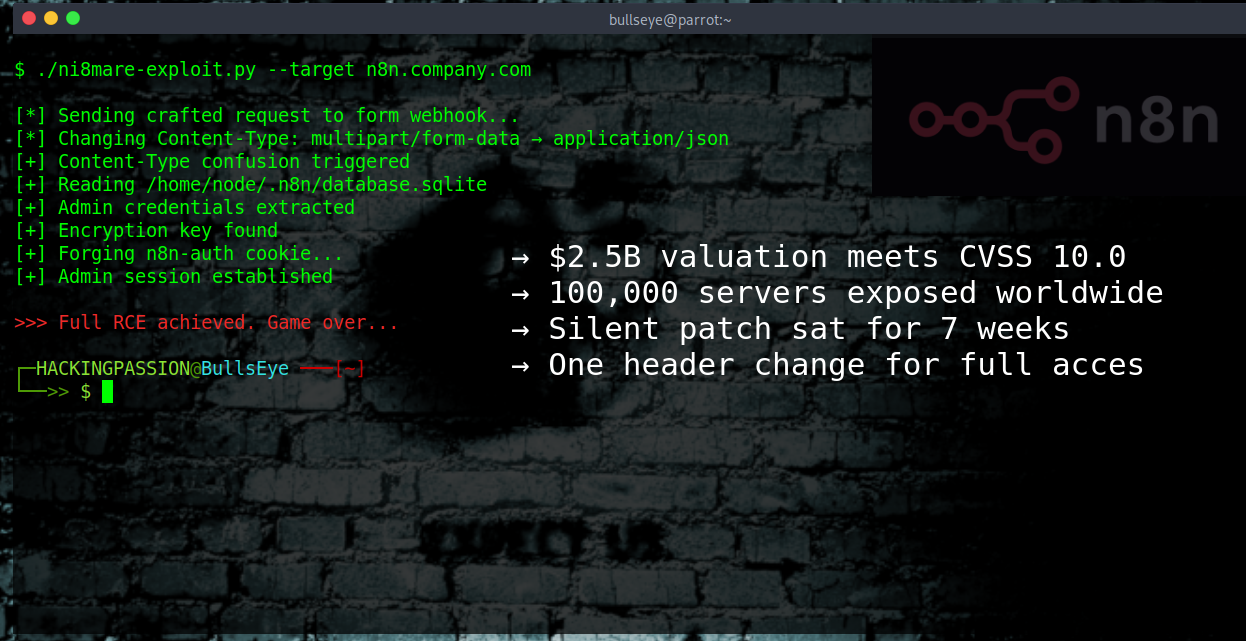
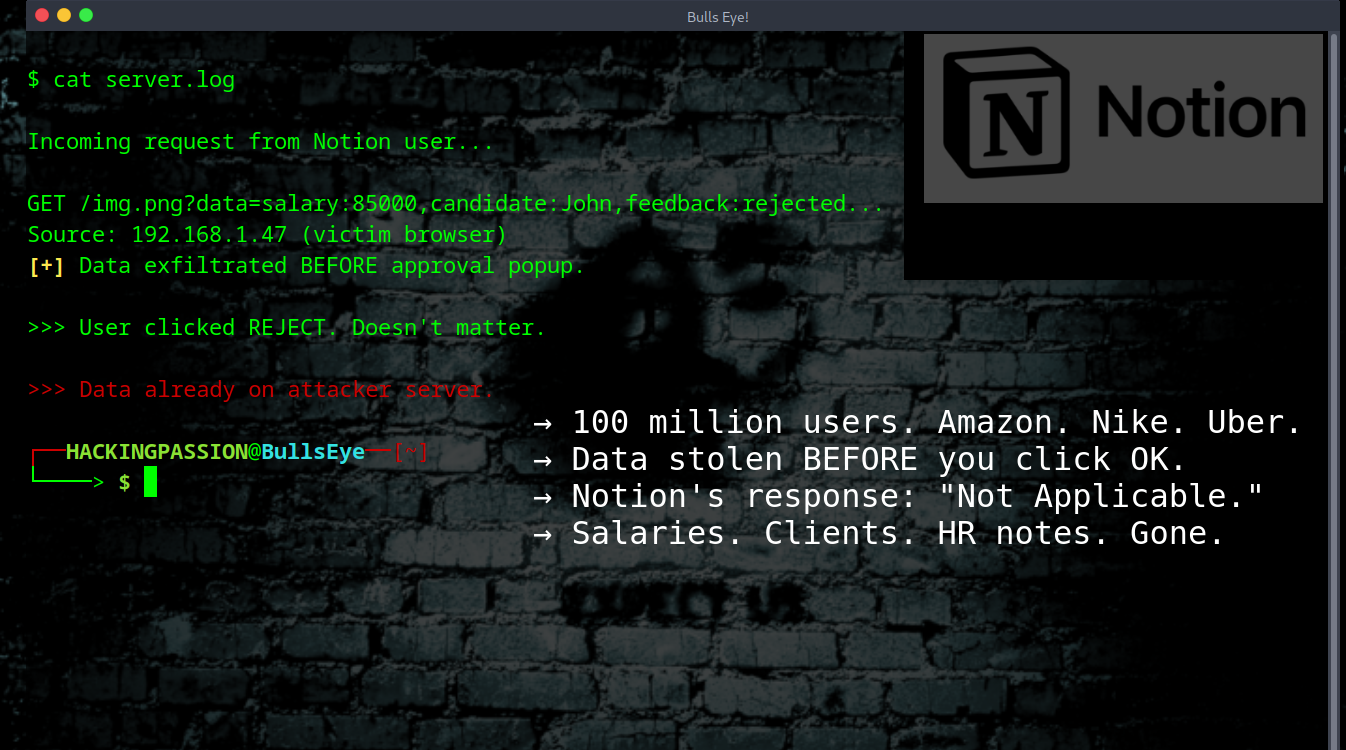
GootLoader Tricks Security Tools Into Seeing a Safe File While Windows Runs Malware
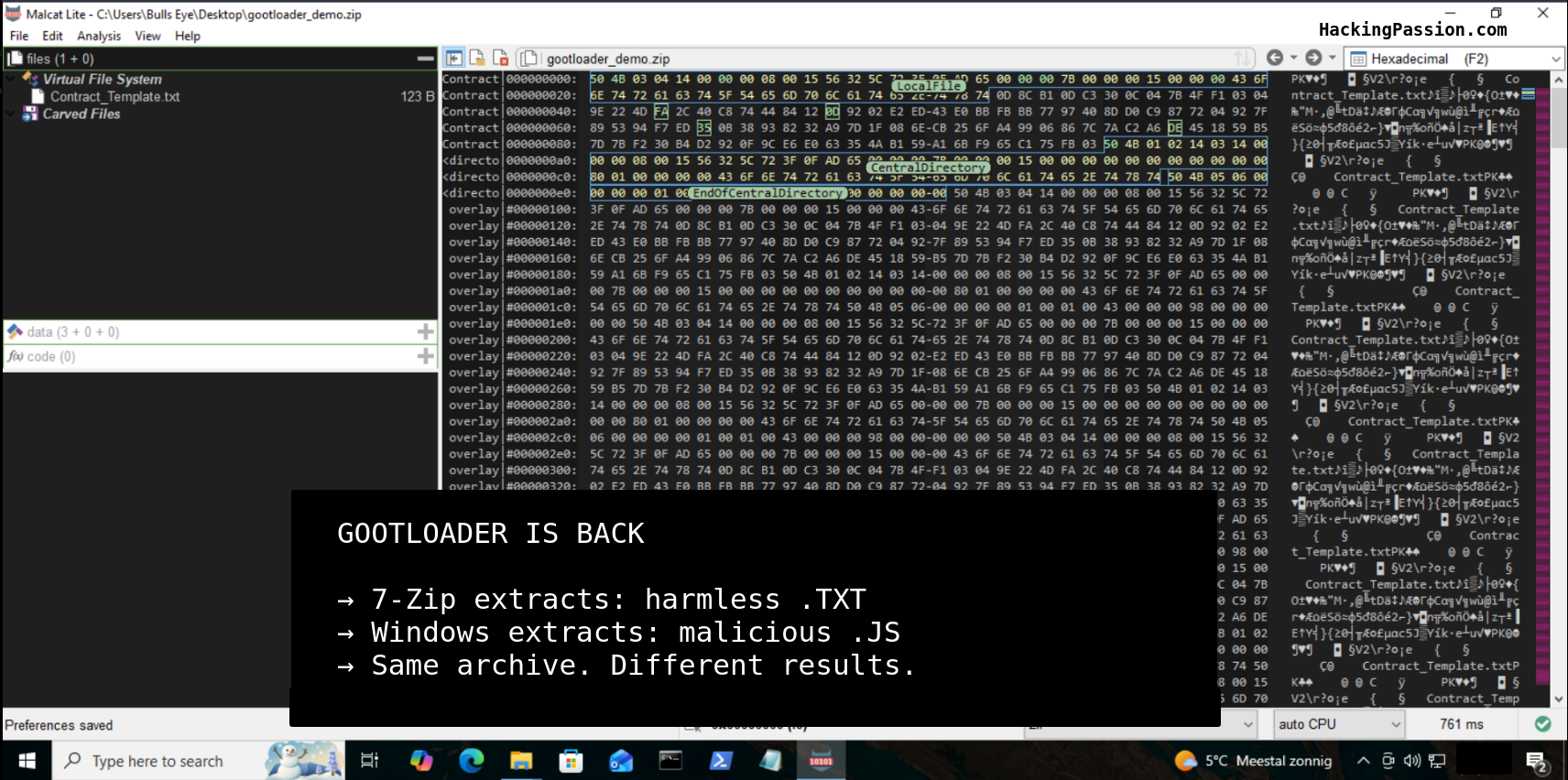
GootLoader is back. This week, researchers discovered their newest trick: a way to make security tools completely blind. Your antivirus scans the ZIP file. Nothing found. WinRAR tries to open it. Fails. 7-Zip tries. Also fails. Corrupted file, right? But when you double-click it, Windows opens it just fine. And now you’re infected. 🧐
The trick is simple but brilliant. They take 500 to 1000 ZIP files and glue them together into one massive file. Most analysis tools read ZIP files from the beginning. They hit the first archive, see garbage, and crash. But here is the thing about ZIP files. They are actually read from the END. The “End of Central Directory” record tells the reader where to find the actual content. Windows knows this. It skips all the junk, finds the last valid archive, and happily extracts the malware.